ScreenConnect Vulnerability Scanner (CVE-2024-1709)
This free ScreenConnect Vulnerability Scanner checks if your ConnectWise target is vulnerable to CVE-2024-1709 and CVE-2024-1708 – aka the SlashAndGrab vulnerabilities. Unauthenticated attackers can exploit these critical vulnerabilities to bypass security controls and get unrestricted access to the affected system.
This ScreenConnect Vulnerability Scanner only scans ports 80, 443 and 8040, which Shodan confirms are by far the most frequently used ports on which ScreenConnect ConnectWise is installed.
If you'd like to perform a full vulnerability assessment of your network assets, this free tool is part of the premium version of our Network Vulnerability Scanner, which detects over 10.000 CVEs using its Deep Scan feature. For full access to it and other 20+ tools, check out our pricing plans.
This free ScreenConnect Vulnerability Scanner checks if your ConnectWise target is vulnerable to CVE-2024-1709 and CVE-2024-1708 – aka the SlashAndGrab vulnerabilities. Unauthenticated attackers can exploit these critical vulnerabilities to bypass security controls and get unrestricted access to the affected system.
This ScreenConnect Vulnerability Scanner only scans ports 80, 443 and 8040, which Shodan confirms are by far the most frequently used ports on which ScreenConnect ConnectWise is installed.
ConnectWise ScreenConnect vulnerabilities - technical details
ConnectWise, a US-based software company, has issued updates to address two critical flaws in its SmartConnect remote management software, one of which is actively being exploited in the wild.
CVE-2024-1708 (CVSSv3 8.4)
This vulnerability consists of insufficient restriction on access to a directory path ("path traversal"), classified under CWE-22.
This path traversal flaw that originates in inadequate validation of directory traversal patterns, can let a remote attacker with elevated privileges dispatch an especially crafted HTTP request to access files arbitrarily on the target system.
CVE-2024-1709 (CVSSv3 10)
This issue allows attackers to circumvent authentication mechanisms through an alternative pathway or method, as per CWE-288.
Specifically, an unauthenticated attacker can use CVE-2024-1709 to bypass security controls and gain unrestricted system access.
What’s more, ConnectWise has reported these indicators of compromise, meaning cyber adversaries are using these specific IP addresses: 155.133.5.15, 155.133.5.14, 118.69.65.60.
This issue is present in versions of ScreenConnect up to 23.9.7.
Huntress, a cybersecurity company, confirmed these vulnerabilities are easily exploitable through a detailed article and video (created by John Hammond) and has devised a temporary solution for affected systems.
About our Network Vulnerability Scanner
Our Network Vulnerability Scanner is a well-rounded tool for all your network security assessments.
It combines multiple engines and fine-tuned (customizable) scan settings which surface over 10.000 critical vulnerabilities, misconfigurations, and outdated services.
Each scan automatically updates your attack surface and provides an up-to-date map for planning targeted attacks or strategic lateral movements.
Explore a sample report which includes a vulnerability summary, automatically confirmed findings, evidence, and more.
See what else it can doFAQ
What is ConnectWise?
ConnectWise is a comprehensive software suite designed to help managed service providers and IT professionals to efficiently manage their operations, including remote monitoring and management, ticketing, billing, project management, and customer relationship management. The suite includes tools for proactive threat detection, incident response, and secure remote access management.
What is ConnectWise ScreenConnect?
ConnectWise ScreenConnect is a remote support and access solution designed to help support technicians to assist end-users with troubleshooting, collaboration, and remote control of devices across various platforms and environments.
What is the potential impact of CVE-2024-1709?
Exploiting CVE-2024-1709 allows unauthorized access to the setup wizard in ScreenConnect instances, potentially enabling attackers to overwrite the internal user database and gain administrative privileges without having to complete the setup process or have a valid license key.
With administrative access, attackers can easily upload and execute malicious ScreenConnect extensions, leveraging this feature to achieve Remote Code Execution (RCE) on the server.
What is the potential impact of CVE-2024-1708?
This path-traversal vulnerability in ConnectWise ScreenConnect versions 23.9.7 and earlier poses a significant risk because it enables attackers to execute remote code or compromise sensitive data and critical systems.
Unlike other vulnerabilities, this exploit doesn't necessarily require an installed extension for malicious code execution, but still needs administrative credentials and access to the Extensions functionality, which makes it less severe as a standalone threat.
What is a path traversal attack?
A path traversal attack is a type of security exploit where an attacker manipulates input to access files or directories outside of the intended scope of the application. This can lead to unauthorized access to sensitive information, execution of arbitrary code, or compromise of the system's integrity.
How do you exploit CVE-2024-1709?
To exploit CVE-2024-1709, the attacker must send a specific request to the endpoint /SetupWizard.aspx/<randomstring>/ within the affected ScreenConnect target.
This action triggers the setup wizard, making it easy to set new credentials. It's important to be aware that finalizing this setup process overwrites the user database, effectively erasing all existing users except for the one the attacker generated.
What port does Screenconnect use?
ScreenConnect typically uses port 8040 in its default configuration, but this port's assignment can be altered during installation.
For instance, a Shodan query (March 5, 2024) shows the distribution of ports among externally facing targets. Among 13967 hosts, the breakdown is as follows:
- Approximately 28.1% are accessible via port
443 - Around 12.6% are accessible via port
80 - Roughly 10.1% are accessible via port
8040.
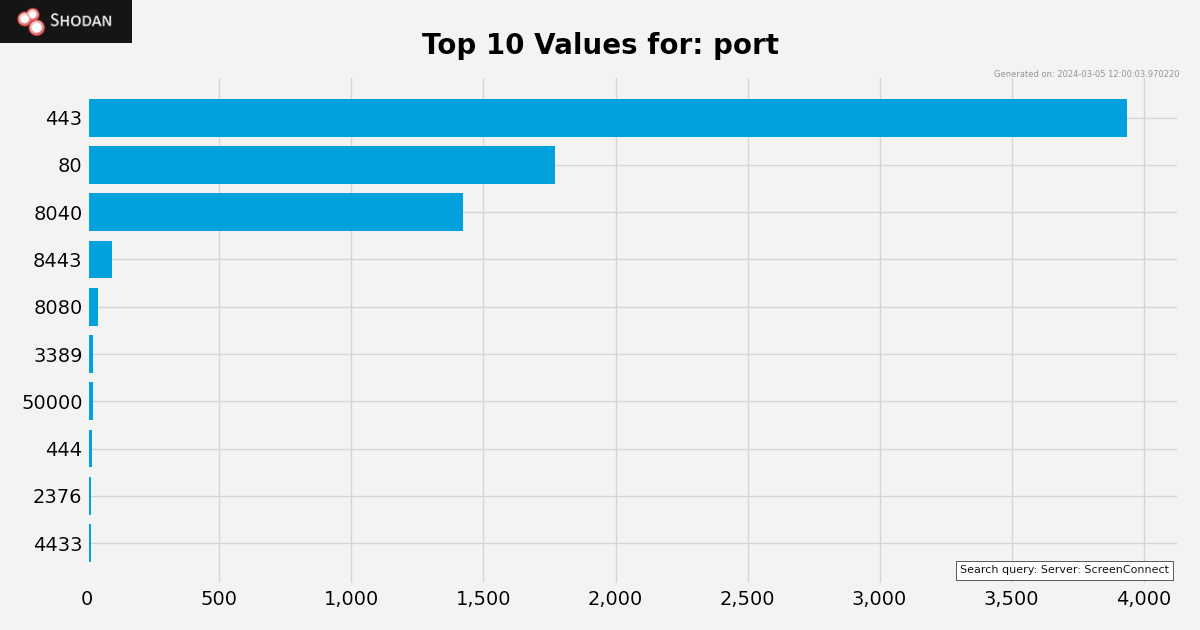
The remaining individual ports collectively represent a minor percentage of the total number of hosts, with some potentially configured as honeypots.
Our free tool exclusively scans ports 80, 443, and 8040.
If you've configured ScreenConnect on a non-default port, you can use the premium version of our Network Vulnerability Scanner to scan that custom port quickly and get a reliable result.