Discover Your Network's Attack Surface
Automatically detect open ports, services, and running software from all your targets. Visualize all results in a central, unified view.
Get an overview of your network perimeter exposure.
Find open ports that shouldn't be publicly accessible.
Detect old and forgotten web technologies.
Automatically created from your tool scan results.
Key Features
Attack Surface View
And how it can help you have a general outlook on a system
In a network environment, all the entry points an attacker could use to access a system combine to create the Attack Surface. It also covers the ways an unauthorized user could send data to a web application and/or extract data from it.
In your Pentest-Tools.com dashboard, the Attack Surface includes a list of all IP addresses, hostnames, operating systems, open ports, services, technologies, and their versions from all your targets. Each workspace generates an Attack Surface specific to the targets in it.
How can a system's Attack Surface be represented?
See all the services open across the network perimeter in one place
Big picture view
Improve decision making
Save time
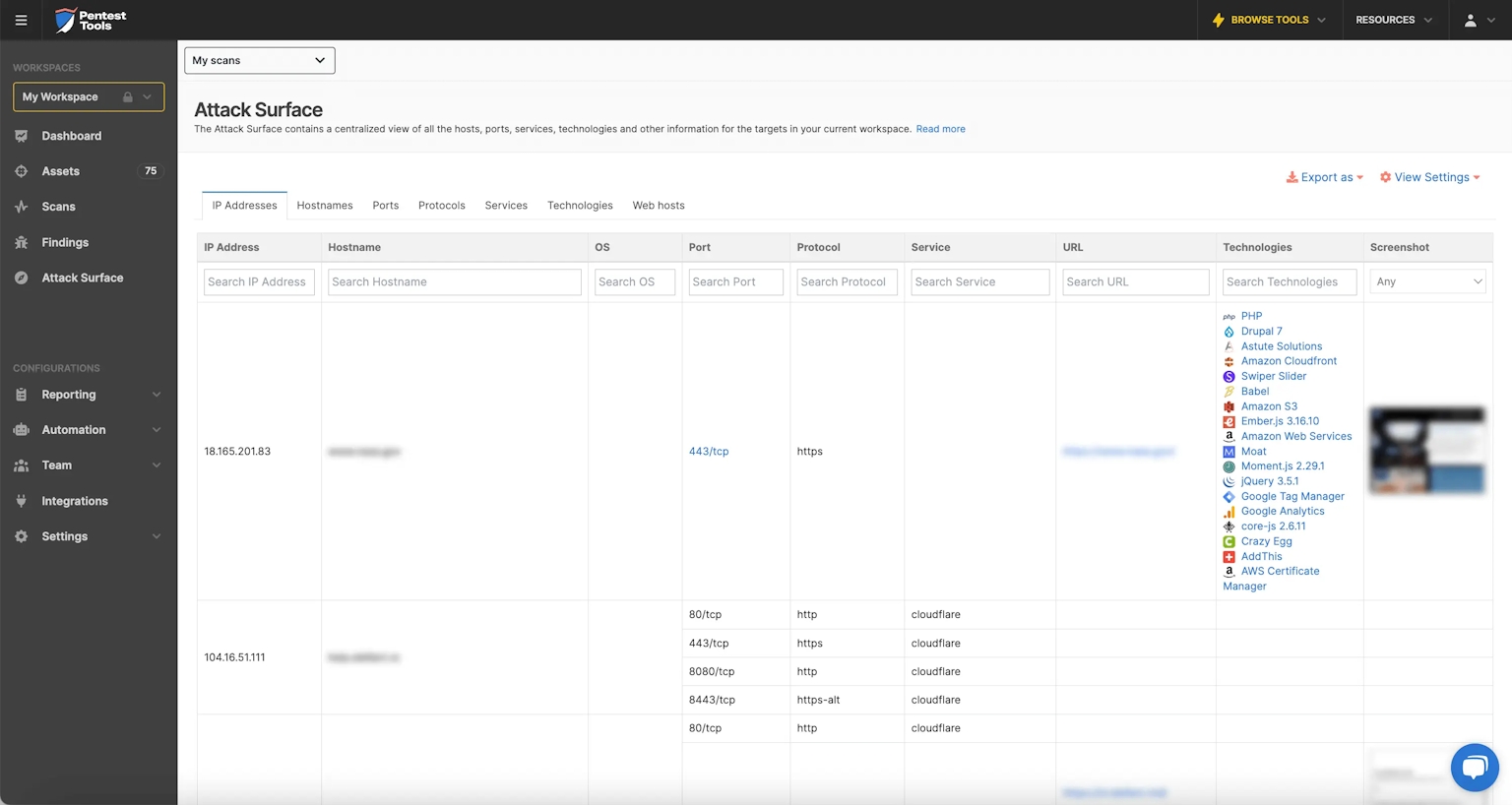
Detect web technologies and spot outdated network service versions
Big picture view
Improve decision making
Save time
Reduce your attack surface based on reliable, up to date data
Always have accurate, up to date visibility into the most vulnerable parts of the system in a flash.
Running a constant cycle of vulnerability scans with the platform enriches and expands your Attack Surface view. Use it to identify risky remote entry points and prioritize decisive, data-driven actions that reduce the target’s exposure to cyber attacks.
Start using the platform today
Unlock the full power and features of our platfom! Compare pricing plans and discover more tools and features.
Use cases
4 ways to use the Attack Surface view
Turn network and service insights into actionable data
Prioritize actions to reduce exposure to attacks
Assess how much work a pentest might involve
Understand how the attack surface evolves in time
Key risks you can diagnose using the Attack Surface
Outdated, exploitable server software
Open ports (that shouldn’t be publicly accessible)
Internal network services exposed on the public network
Old and forgotten web technologies
Developed for
Pentesters
Network security specialists
DevOps teams
Developers
Pentesters
Business owners
FAQ
Common questions
Currently, the following tools generate data for the Attack Surface: Website Recon, Website Scanner, TCP and UDP Port Scanner and OpenVAS Scanner.
We plan to add data for other tools and scanners at Pentest-Tools.com in future iterations. Keep an eye on our changelog, blog, and on our LinkedIn page to be the first to know when we do! You can also explore more details in the dedicated article in our Support Center .