Detect ProxyShell (pre-auth Microsoft Exchange RCE) with Pentest-Tools.com

- Article tags
On-prem Microsoft Exchange servers have created a lot of work for IT and security specialists in the past months.
In March, ProxyLogon left servers vulnerable to Server-Side Request Forgery through CVE-2021-26855, so we launched a dedicated scanner for it.
In May, #proxynotfound popped up, so we integrated detection for it into our Network Vulnerability Scanner to make detection and reporting faster.
Now bad actors are racing to exploit ProxyShell, an attack chain that exploits three CVEs to get Remote Code Execution on the target host:
CVE-2021-34473 – Pre-auth Path Confusion leads to ACL Bypass
CVE-2021-34523 – Elevation of Privilege on Exchange PowerShell Backend
CVE-2021-31207 – Post-auth Arbitrary-File-Write leads to RCE
Web and Application 0-day researcher Orange Tsai presented ProxyShell at Black Hat US 2021 and, once public, the technical details attracted ethical hackers and malicious ones alike.

As often happens with these vulnerabilities and the attack chains that increase their negative impact, a flurry followed. Pentesters and defenders are rushing to detect, report, and patch vulnerable targets while cybercriminals focus on installing web shells and gaining persistence.
Detect the ProxyShell attack chain with Pentest-Tools.com
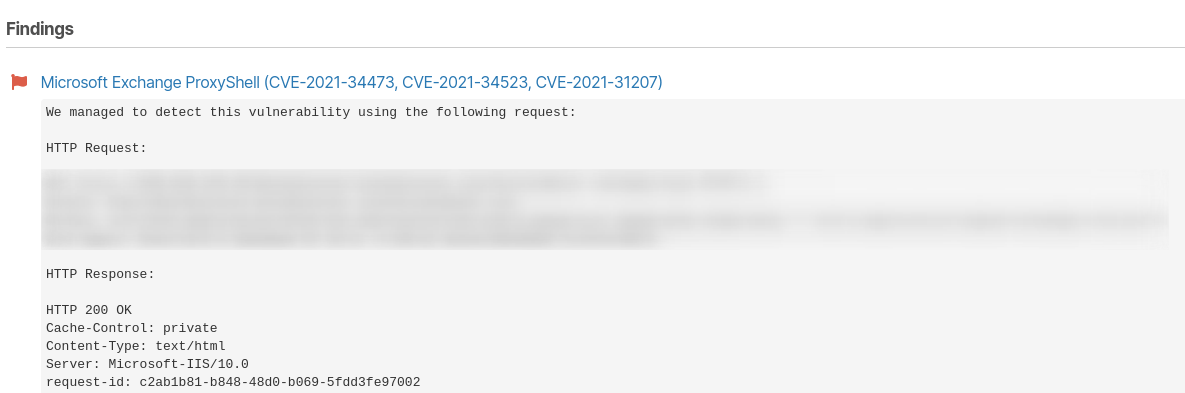
If your scans with our Network Vulnerability Scanner reveal vulnerable targets, you get a ready-to-go report that’s pre-filled with risk descriptions and recommendations.
Here’s what the sample report looks like:
And here’s a preview of the recommendations section:
Applying the latest Microsoft patch for the Exchange Server fixes this vulnerability.
If the affected server was exposed to the Internet, we recommend looking for indicators of compromise (IoCs), as there is a high probability malicious actors have already compromised it.
Scan your targets in minutes
Exploitation interest remains high and an estimated 13.000 Exchange servers are still vulnerable, according to the latest data:
proxyshell – short summary and vulnscan-results
https://t.co/UdOeTHD0Fk #dfir #proxyshell pic.twitter.com/rMQfZqUmU4
— ZeroBSGmbH (@zeroB_S) August 11, 2021
Updates
Later edit [Aug 12, 2021]
The news cycle may have gotten over ProxyShell, but bad actors definitely haven’t.
More than 18% of Exchange servers remain unpatched for the ProxyShell vulnerability. Nearly 40% are vulnerable to CVE-2021-31206
https://t.co/7yetz9GoJw pic.twitter.com/0r2AOQsibB
— Shodan (@shodanhq) August 11, 2021
It doesn’t make things easier for defenders that exploiting ProxyShell doesn’t require any credentials and can be triggered on port 443, which is used by Exchange’s Client Access Service (CAS). However, it does make it really appealing and handy for malicious attackers.
A reminder on the business value of on-prem Microsoft Exchange servers: company email servers hold business secrets, confidential conversations, and attachments, and pretty much are the lifeblood of organizations.
A motivated cybercriminal knows how to take advantage of access to the server to monetize it in many ways (extortion, data exfiltration, and selling, recon for subsequent attacks, stepping stone for a supply chain attack, Business Email Compromise, etc.).








